The Dark Web is a mysterious place. Once you leave the relative safety of the traditional internet, things can get pretty scary. But, you might not know there are things on the Dark Web that the government is working to keep confidential. The secrets might just blow your mind.
Are hackers in your phone? Here’s how to find out
I’ve heard from many people who have been cyberstalked over the years. Sadly, today’s tech makes it all too easy.
Take Apple AirTags, for example. They’re cheap, small, and easy to hide — and can tell the owner exactly where you are located. Here are six signs to look for if you suspect someone is tracking you this way.
Then there are the people convinced someone is listening in on their calls or reading their texts. Sometimes, I believe something is going on. Other times, paranoia has set in. Here’s how to know if you’re being stalked or are just paranoid.
It’s not always easy to tell if your phone has been compromised. Here are some tips for diagnosing a hacked phone.
How does this happen in the first place?
A person doesn’t necessarily have to be a hacker to get into your phone. Someone can hold your phone to your face when you’re sleeping and unlock it. This one act lets them snoop through your device without your knowledge.
Then there’s software that does the job. Stalkerware is designed to track you using GPS, call logs, messages, images, browser history, and more. This software can be hidden behind another app that seems harmless. Tap or click for six signs stalkerware could be on your phone.
There are harmful files and malicious links that can infect your phone without your knowledge. Something as innocuous as a PDF file can carry some poisonous data. That’s why it’s so important to be careful what you click.
What about apps? Sketchy downloads can imitate well-known apps or try their luck to trick you into downloading and running them. Once you do so, your phone is infected with malware.
There’s also a method called SIM swapping that is much more targeted. A criminal calls your phone carrier pretends to be you, and requests a new SIM card — disconnecting your old line and transferring everything to the criminal’s device.
Tap or click for three ways to stop this scary attack.
Look for the signs
5 ways to think like a hacker, starting today
The more we rely on our devices, the more vulnerable we are to attacks and scams. Your smartphone is a prime target. Tap or click here for three ways to secure it from hackers.
It’s not just passwords and sensitive details you need to protect. Think about all the photos and videos stored on your phone that you would be heartbroken to lose. Tap or click for the best ways to save your phone’s photos before it’s too late.
5 silly mistakes putting your online privacy and security at huge risk

There are so many online scams and tricks out there I can’t cover them all on my website and national radio show. I make it my duty to inform you of the tactics bad actors use to fool you.
A great podcast was the episode when I dove into the mind of a hacker. Tap or click to listen to an episode of my podcast, Kim Komando Today, with an IBM social engineer. She spills the secrets hackers use to scare and confuse people.
Antivirus vs. VPN: Do you need both for online privacy and security?
You probably know that bad guys lurk within every corner of the internet. You have to watch out for spyware, ransomware, phishing attacks, IoT invasions and more. Oh, and don’t forget “zero-click attacks.” Researchers recently discovered hackers used military-grade spyware to remotely access iPhones and even replicate their data.
Here’s what it looks like when a virus takes over your computer
A slow computer can turn you into a detective. You start investigating the clues, trying to find out what happened. You might even Google “How to tell if you have a virus” or “Warning signs your computer is infected.”
6 apps that could make a difference during an emergency

Have you ever been stuck in the middle of an actual emergency? Tap or click here for 18 must-have items that help you survive any crisis.
Not every calamity takes place at home. You never know when you’ll be facing something dire with only your smartphone in hand.
8 signs that your computer has been hacked

If your device is connected to the internet, it’s vulnerable to hacks. It’s as simple as that. Cybercriminals are always coming up with new tricks to get into your gadgets and you should be aware of that.
Fortunately, there are usually signs that your device has been compromised. When it comes to smartphones, this can include spikes in data usage, battery drainage and changes to your home screen, among other indicators. Tap or click here for information on diagnosing and solving phone hacks.
Giving up Kaspersky? Get a year of Kim's antivirus pick for only $19

With tensions mounting across the world during the Russia-Ukraine War, cybersecurity experts warn not to use Russian-owned Kasperksy antivirus protection. Here’s why.
A question I get time and time again is, “What’s your antivirus recommendation?” Whether you’ve never used antivirus, stopped years ago, or want to get rid of Kaspersky, I can help.
Crypto tip: Simple mistake costs man $120K – Don't let it happen to you

You’ve probably heard of cryptocurrency, the digital medium of exchange that has become a darling of social media influencers. You don’t need to be a crypto investor to know that there’s no such thing as easy money and that crypto, in particular, is an especially risky investment.
Your ISP is watching — Here's what it knows about you
You probably know by now that your internet service provider watches what you do. After all, a tiny bit of surveillance helps these companies provide the best services possible. But many ISPs collect data beyond their scope, according to a new report from the FTC.
Free check to see if your router has been hacked by criminals

The internet is a crazy place. Not only do marketers and advertisers follow your every move, but there are also hackers and scammers lurking in the dark corners, ready to pounce on your personal information.
At least marketers and advertisers want to make money off of you. The hackers and scammers we’re talking about want to flat-out steal your money by hijacking your personal information.
The government doesn’t want you to know these Dark Web secrets
What's on the Dark Web? These are the top 5 sites in 2021
When most of us think of the Dark Web, our mind goes straight to the worst-case scenarios. We think of assassins, poison, illegal drugs and creepy red room videos. But these hidden corners of the internet aren’t all darkness and depravity.
9 popular routers are at risk - See if yours is on the list

Your router is arguably the most critical component in your internet network. It serves as the primary point where all wireless devices connect and download information. A vulnerability in the router’s software could spell disaster. Tap or click here if you are sick of slow Wi-Fi speeds.
5 common VPN issues and how to fix them

VPNs, or virtual private networks, are typically set and forget services that don’t require a lot of troubleshooting. Unfortunately, this doesn’t mean there aren’t problems with VPNs you might have to address from time to time.
Security tip: How to set up a VPN on all your devices
If you’re security and privacy-conscious, you need to take all the steps you can to keep yourself safe online. That starts with the right VPN.
Not using a VPN is like leaving your front door unlocked every time you go out. Sure, nothing might happen for years, but when something does happen, it’s devastating.
Google is making a major security change for all users – Check your settings
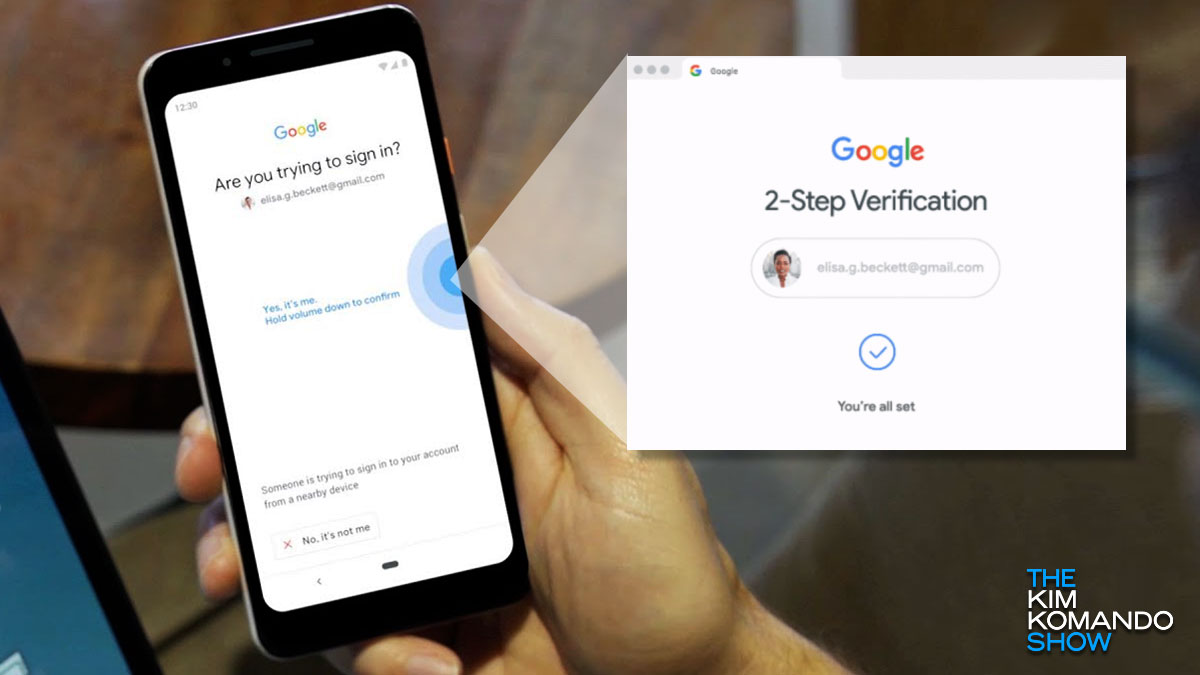
Strong passwords are a given when it comes to protecting your accounts, devices and data, but that’s not enough. Cybercriminals are relentless, and you can never have too much protection. That’s where two-factor authentication comes in. 2FA adds an extra layer of security when you log in to an account or unlock a device.
Getting into crypto? A browser extension is draining unsuspecting users' accounts

Cryptocurrencies like Bitcoin have seen a massive explosion in popularity over the last few years. The price of a single Bitcoin skyrocketed exponentially since its introduction, driving many people to dabble in the virtual crypto money unit.
Did you forget your password again? Try this

Most websites ask for a username and password, but it isn’t safe to use the same ones for every site. You also have to consider what kind of passwords are the best to keep hackers out of your accounts. Tap or click here for five tips to secure your accounts.
Reader question: ‘Are all VPNs the same? Which one should I go with?’

I recently received a great question from a reader named Jim. He wanted to know about VPNs, and I think this is something many folks may be unclear about.
“I have a question about iPhone security. Are all VPNs the same? Or is one better than the other?” He went on to say that his phone has been compromised in the past.