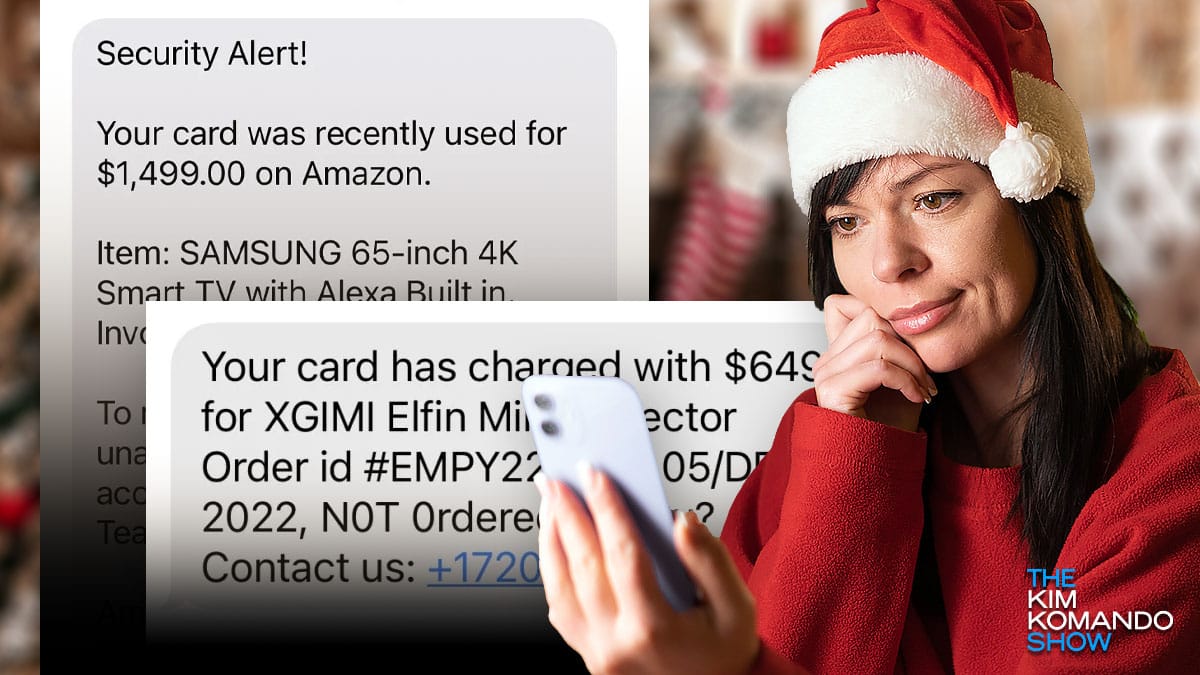
Shopping scams are getting nastier: One victim in Maryland was tricked into paying a fake $0.99 “redelivery fee” and ended up losing $400. USPS and other shipping companies won’t add a shipping charge after the fact. These scams usually come via text, so watch out.
How apps you use got hijacked into selling your location

Playing Candy Crush, swiping left on a dating app and checking your Yahoo inbox shouldn’t expose your location. I say shouldn’t, but those apps and thousands more were likely hijacked by data brokers who turned your personal info into cash.
Now, cybercriminals on the Dark Web have access to the location information of tens of millions of people. I’ll explain how this happened and share my secret weapon for fighting this kind of privacy invasion.
🔎 Whodunnit?
It all started with Gravy Analytics, a data broker that tracks over a billion devices worldwide. (They also own Venntel, which sells info to U.S. government agencies like the FBI and IRS.) A Russian hacker wormed into Gravy’s records, stealing 1.4 gigabytes of info.
▶️ That data includes over 30 million location points. 404 Media (paywall link) investigated the breach and found the shocking way they obtained your whereabouts.
This is clever (and super sketchy)
When you open a site or app, there’s a millisecond-long auction to decide the ads you see. The process is called real-time bidding (RTB), and it’s based on, among other things, all the data points they have about you and what you’re most likely to buy.
RTB collects enough information to make sure the right people are seeing an ad, and data brokers are in those auctions, too, with another purpose: To snag your info. The scummiest part is they don’t even need to buy any ads to do it.
The Gravy Analytics leak data shows thousands of apps gathered your location data. The working theory is they collected RTB data themselves or bought it from other data-broker companies.
Who’s on this list?
The list is long, and I’ll get to the specifics. Some apps, like Tinder, say they’ve never worked with Gravy Analytics. (I’ve heard that excuse before.) But if the info came from RTB, that’s in the advertising ecosystem, not the app’s code.
Really, that’s worse in some ways. This type of location tracking is happening through apps whether or not developers explicitly OK it. This includes:
6 signs your vacation rental is a scam

It’s that time of year when so many of us are planning vacations and booking a rental. Sadly, scammers are very aware of that, and they’re always changing their tricks to fool people out of their money, rentals — or worse.
Wait, are public phone chargers dangerous?

Those charging kiosks in airports, hotels and malls are so tempting when you’re out and about with a dying phone. Their owners promise they’re safe. The government disagrees, and so do I. Groan, I know.
Welcome to the newest phase of juice jacking. The phenomenon has been around for more than 10 years. Hackers use public phone-charging stations to upload malware to your devices. Then, they ransom your device or steal your passwords. Super-duper.
It’s time to replace your old router

Most folks don’t know their wireless router — that handy dandy device alongside the modem that connects your devices to the internet — has a shelf life. Once it hits the three-year mark, you’re due for an upgrade.
Free VPN risk: Check this list of 9 infected apps

I’m cheap and try to save a buck wherever I can. I use all my credit card perks, always click the coupon boxes on Amazon, and, to my husband’s great annoyance, cancel streaming services the minute we stop watching them.
A New Jersey family is living a nightmare

It started back in September. Dan in Bridgewater, New Jersey, had his bank account hacked. Their first step was to withdraw money and apply for a loan. In October, he got a letter from TD Bank notifying him of an address change on his account.
Every parent should read this

This topic hits me personally, and I don’t like to discuss it at all. You never know who’s a child predator. I was molested by a trusted family friend when I was 6 years old. I told my parents, and they took immediate action — well, not the action my Dad wanted, which was to cut off the guy’s hands.
It’s not just bogus calls and emails

Imagine getting a call from what looks like your bank’s number, warning you about suspicious activity on your account. The caller knows just enough to make you trust them. It’s all a lie, and you’re screwed if you don’t realize that soon enough.
Scammers are targeting teens – Warn your Gen Zer about these tricks

I told you about the 14-year-old who committed suicide after following the advice of an AI chatbot. Another family is suing the same one — Character AI — after it told an autistic 14-year-old to kill his parents. It also exposed an 11-year-old to sexual content.
Your IP address: What it is and why you need to protect yours if you care about privacy

Using the internet is a complicated affair. It may not feel like that to you as a user. You click on your browser and get on with your day — it’s as easy as pie.
Behind the scenes, though, is a whole different story. It’s full of numbers like your Internet Protocol (IP) address, basically your digital home address. This numeric label distinguishes your phone or computer from other devices worldwide.
How to install antivirus and scan your computer

If you’re online, you’re at risk, plain and simple. There’s more out there after your info and wallet than you realize, from phishing scams to ransomware and malicious apps to malware.
That’s why it’s critical to protect your personal and business devices correctly. When it comes to your computer, tablet and phone, you need a robust security suite.
🔒 Friendly reminder: Browser extensions lose support and change developers. Take a minute to review what’s installed and ditch anything you don’t use. On Chrome, tap the three dots near your profile icon, hover over Extensions, then select Manage Extensions. On Safari, go to Preferences > Extensions.
5 clever tricks holiday scammers use
JD in Dallas emailed me with a story. He and his wife were at the mall and stopped for a Christmas selfie. Two young men walking by offered to take the pic for them — and one kept wiping the phone’s lens inside his jacket.
Set up your Wi-Fi for easy sharing with guests

You’ve got a turkey in the oven, presents need to be wrapped, and your cousin’s kid screams (again), “What’s the Wi-Fi password?” You’re juggling a hundred things at once, and the last thing you want to do is to spell out your password.
Security tip: Next time you stay at a hotel, turn on your VPN

Did you know the average American spends more than 24 hours each week online? That is a considerable chunk of time.
If you’re one of many with multiple devices regularly accessing the internet, you probably know you need a secure connection to protect sensitive data. A virtual private network or VPN is the best way to do this.
Why you can’t access some sites while you’re on a VPN and what to do

Let’s say you’re browsing the web with a VPN. You’re protecting privacy, so you’re confident hackers and advertisers can’t track you. Then you try to go to a site, and it just won’t load.
This can throw a wrench into productivity when working. Or it can ruin your mood when trying to have fun online.
Antivirus comparison: Which option is best for your PC or Mac?

If you browse the internet regularly, you can’t get around the fact that you need antivirus software. Viruses can pop up in unexpected places, and you want your device to be able to fight one off if it appears.
Dangerous malware making the rounds is what makes having antivirus software protecting you so critical. But what’s the best antivirus software for a Mac or Windows computer? Keep reading to see the best options.
Malware warning: Red flags your computer is under attack

It’s Computer Security Day, and there’s no better time to remind you malware is lurking everywhere. From phishing emails to unsuspecting ads, just one wrong click can compromise your personal info or infect your devices.
These passwords take 1 second to crack

Here’s a wild stat: 78% of the world’s most common passwords can be cracked in less than a second. The most-used password in the world, “123456,” has been leaked more than 3 million times. And get this: 1.2 million of those were corporate passwords.