Who’s the most hated tech billionaire? Hint: It’s not who you think. Plus, Amazon wants you to pay $19.99 a month for a premium Alexa. Google scraps two-factor authentication, and comedians are blowing up on LinkedIn.
Your IP address: What it is and why you need to protect yours if you care about privacy

Using the internet is a complicated affair. It may not feel like that to you as a user. You click on your browser and get on with your day — it’s as easy as pie.
Behind the scenes, though, is a whole different story. It’s full of numbers like your Internet Protocol (IP) address, basically your digital home address. This numeric label distinguishes your phone or computer from other devices worldwide.
When you type in a website, your computer translates that into numbers, searching the site’s IP address and loading it onto your screen. Just as money makes the world go round, so, too, do numbers keep the internet chugging along. But your whole digital world can crash when someone snatches your IP address.
An exposed IP address puts you in danger
Your IP address plays a significant role in sending and receiving data online. It’s tied to sensitive information, like your online identity and location. If someone tracks down this number, they could use it as a starting point for nefarious purposes.
Sadly, it’s easy for strangers online to find your IP address. It’s a huge vulnerability: They could hack your device or steal your identity. Or they could enter your address into a free tracking website like iplocation.net to find out where you live. It even comes with a built-in map:
A lot of people on social media apps will doxx one another. Suppose you comment that you like pineapple on pizza on Twitter. Someone having a bad day might respond by tracking down your IP address, posting your name and address and calling their followers, like “Let’s protest in front of their house.”
Of course, that’s a light-hearted example. Reality can be much grimmer.
And get this: Tracing someone else’s IP address is legal. Authorities only intervene when people use one another’s IP addresses for crimes. All the apps and websites you use collect your IP address and other private data.
So, how does someone find out your IP address?
First, they could try to impersonate you. For instance, a hacker could break into a vulnerable social media account if you aren’t using two-factor authentication. If you reuse passwords, they could break into even more accounts until they reach one with sensitive data. Then, it’s a free-for-all with your private info.
Hackers can collect your IP address if you connect to a vulnerable public Wi-Fi network. They can even be nefarious and create a link that gives away your IP address upon clicking it.
Bad news: Here's how much your social media logins cost on the Dark Web
What if I told you for just $12, someone could buy your Instagram login. They could read all your messages, look through everything you’ve “liked” and even post as you.
Whizcase gathered prices from Dark Web marketplaces to see how much your online identity is worth, and it’s grim.
March 1st, 2025
Lost Social Security card? Starting this summer, the Social Security Administration will let people with “my Social Security” accounts see their full Social Security number online. It keeps your physical card safe from theft, but might open a can of worms courtesy of hackers. Don’t forget to secure it with two-factor authentication!
🔒 Garage security trick: Thieves can hack garage door openers, but there’s a clever fix. Use a smart plug to cut power to the opener. It’s like two-factor authentication when you’re away. Here’s a four-pack ($21% off). Need to open it late? Just turn the plug back on with a voice command or your app.
We may earn a commission from purchases, but our recommendations are always objective.
Use this home security camera buying guide to be safer at home
Here’s a conundrum: Your security camera could expose you to data breaches. Last year, a security researcher found that Eufy cameras uploaded private images to the cloud.
Anker recently admitted to storing images and video feeds in the cloud without users’ knowledge. This popular security cam manufacturer recently didn’t even encrypt the private content. That means anyone could have seen your personal images through your Anker devices.
Firewall vs. antivirus: What's the difference and do you need both?

When it comes to protecting yourself online, there’s a lot of confusion. Between VPNs, two-factor authentication, antivirus software and firewalls, there are so many ways to protect yourself that it can be hard to track them all.
iCloud+ subscription? Buy a custom email like you@yourname.com from your iPhone. All you need is an iCloud Mail account and two-factor authentication turned on. Then go to Settings > [your name] > iCloud > Mail > Custom Email Domain > Continue > Buy a Domain. Search for the domain name you want, pick it if it’s available and follow the prompts to buy it. Neat.
RIP SMS 2FA: Translation if you’re totally confused: Google is ditching text message (SMS) two-factor authentication (2FA) for something more secure. Now you’ll scan a QR code. Why the change? It’s way too easy for scammers to intercept texts and hack accounts.
What is Skibidi Toilet?
Kids are hooked on toilets that dance and sing. Skibidi Toilet is the latest bizarre trend taking over their screens — we break it down for adults. Plus, Walmart’s body cam program, hidden risks of two-factor authentication, and why Gen Z needs a ride to work from Mom and Dad.
Are hackers in your phone? Here’s how to find out
I’ve heard from many people who have been cyberstalked over the years. Sadly, today’s tech makes it all too easy.
Take Apple AirTags, for example. They’re cheap, small, and easy to hide — and can tell the owner exactly where you are located. Here are six signs to look for if you suspect someone is tracking you this way.
2FA-stealing malware, update your phone, wheels vs. doors
Smartphone malware is getting worse. A variant can steal passwords, bank details and your two-factor authentication codes. Plus, updates for iPhone and Android are here and Allie has the best reasons to update. Also, the crew takes on the debate captivating the internet right now: Are there more wheels or more doors in the world?
2FA-stealing malware, update your phone, wheels vs. doors
Smartphone malware is getting worse. A variant caught stealing passwords, bank details and lots more has a new trick — collecting your two-factor authentication codes. Plus, updates for iPhone and Android are here and Allie has the best reasons to update. And the crew takes on the debate captivating the internet right now: Are there more wheels or more doors in the world?
Crypto tip: Simple mistake costs man $120K – Don't let it happen to you

You’ve probably heard of cryptocurrency, the digital medium of exchange that has become a darling of social media influencers. You don’t need to be a crypto investor to know that there’s no such thing as easy money and that crypto, in particular, is an especially risky investment.
Google is making a major security change for all users – Check your settings
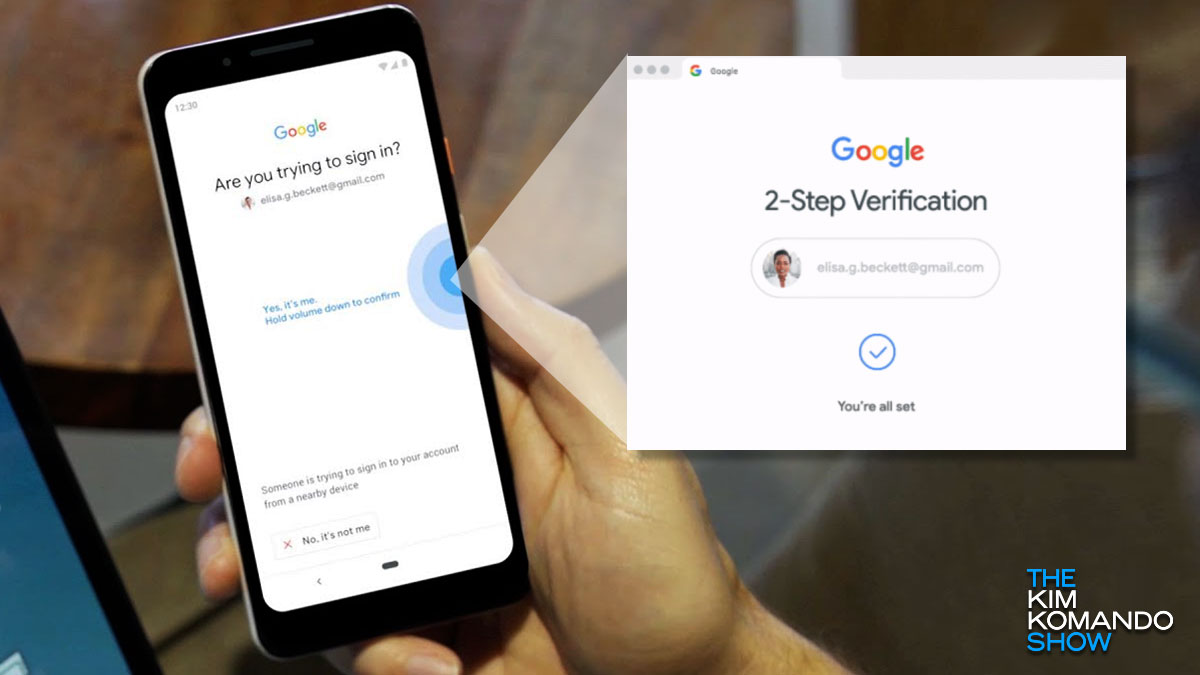
Strong passwords are a given when it comes to protecting your accounts, devices and data, but that’s not enough. Cybercriminals are relentless, and you can never have too much protection. That’s where two-factor authentication comes in. 2FA adds an extra layer of security when you log in to an account or unlock a device.
These are the 20 worst passwords you can use

It’s a tough balancing act to create a password that’s both strong and easy to remember. If you make your passwords too simple, you can actually put your accounts in danger of cyberattacks.
The strongest passwords always use a complex arrangement of numbers, letters and symbols that make them tricky to guess. If you don’t repeat characters, it can also be difficult for hackers to brute force them. Tap or click here to see our guide to stronger passwords.
6 privacy and security mistakes you’re making on social media

Pop quiz: What percentage of American adults use social media? Think about it and I’ll tell you the answer below.
From Facebook to Twitter to Instagram and all the sites in between, we’re voluntarily giving out more information online than ever. Tap or click to get a closer look at exactly what Google knows about you and the steps to erase it.
Your passwords are exposed - here's what to do about it

Pop quiz: How many passwords do you use online? It’s probably more than you can remember right away, and most of the world is right there with you. According to a report from cybersecurity firm Digital Shadows, the average person uses 191 services that require passwords — and more than 15 billion stolen credentials are in circulation. That’s a 300% increase since 2018!
Billions of passwords for sale on the Dark Web - this one was used 7 million times

How tough are your passwords? Despite what you may think, the best password practices from 10 years ago won’t cut it today. If you share passwords across different websites, for example, it’s time to get busy changing them for the sake of your security.
Working from home? You need a VPN now more than ever

You’ve heard Kim talk about how important it is to have a virtual private network (VPN). Now that a lot of you are working from home, it’s even more important to choose a VPN you can trust.
The coronavirus pandemic has prompted many companies across the U.S. to have employees work from home (WFH). That means it’s not just the personal information stored on your device at risk from security threats, but also your work data.
